IT & CYBERSECURITY INSIGHTS
- by Epoch Team
- Posted on January 30, 2026
Posted under:
Security
- by Epoch Team
- Posted on December 5, 2025
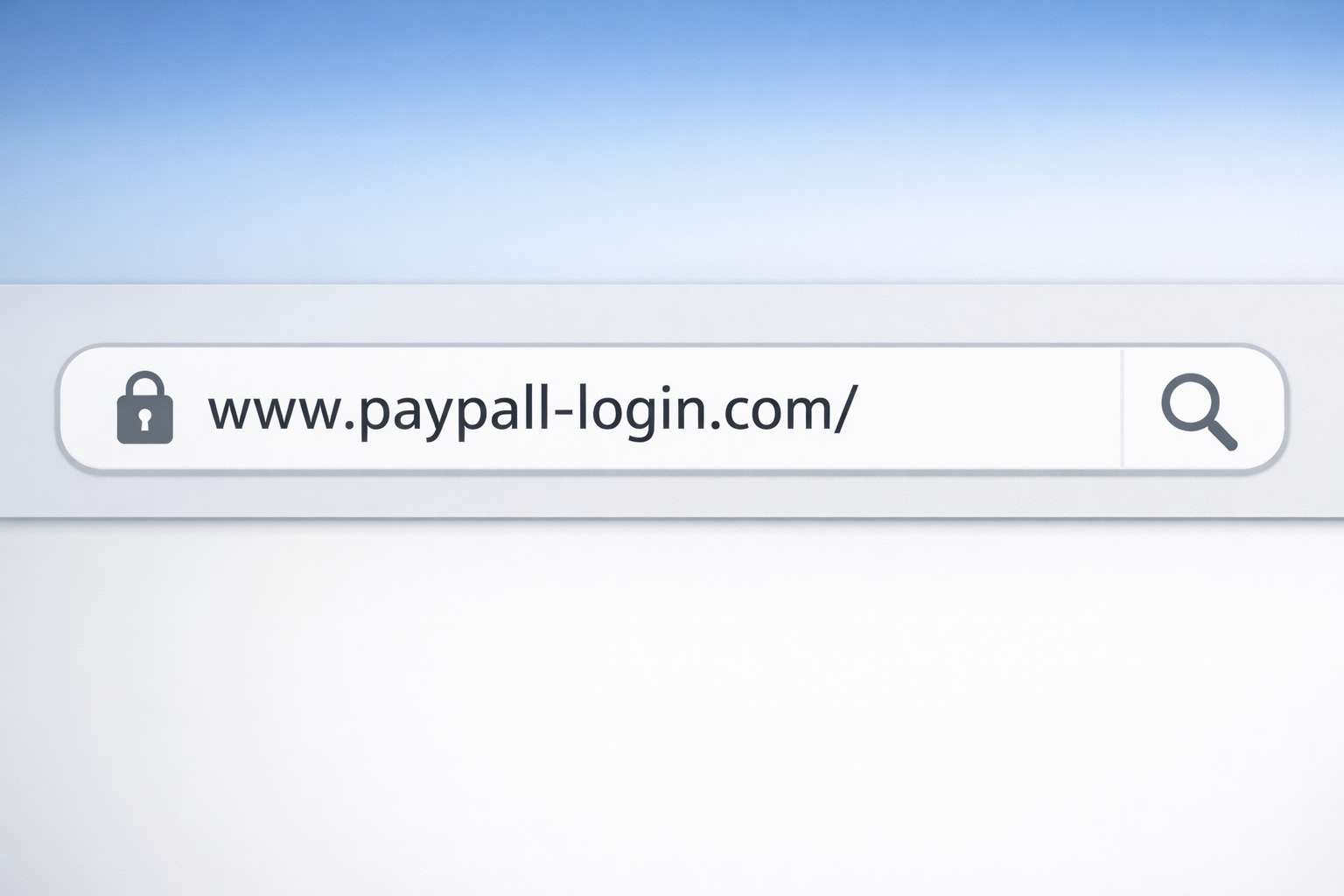
In recent weeks, our team has responded to a growing number of incidents involving a new social-engineering tactic...
Posted under:
AI
- by Epoch Team
- Posted on August 11, 2025
AI tools are everywhere, but many businesses are using them without knowing what’s under the hood. The wrong platform...
- by Epoch Team
- Posted on June 11, 2025
Work-from-anywhere is here to stay—and cybercriminals know it. Whether you’re logging in from a coffee shop, your home...
- by Epoch Team
- Posted on June 10, 2025
Cybercriminals no longer need advanced tools or complex code to breach your systems. Instead, they target something far...
- by Epoch Team
- Posted on May 13, 2025
The cloud has redefined how businesses operate—making it easier to collaborate, scale, and stay competitive from...
- by Epoch Team
- Posted on April 8, 2025
Think back to the last time your business was thrown off course by an unexpected IT issue.Maybe it was a server that...
- by Epoch Team
- Posted on April 7, 2025
Financial firms depend on secure, reliable, and efficient IT systems to stay productive, meet compliance standards, and...